Metasploit Introduction
Welcome Again ! In this write-up we will discuss introduction to the main components of the Metasploit Framework. This room provided on Tryhackme talked about a lot of things : Exploits , payloads , Auxiliary , Encoders , Evasion , NOPs , etc ...
Acutally this is a good introduction for those who start their journey in CyberSecurity and Penetration testing . Good luck !
Details about the room :-
Title : Metasploit Introduction
Description : An introduction to the main components of the Metasploit Framework.
Here we go ...

===========================
Task 1 : Introduction to Metasploit
No Answer Needed
===========================
Task 2 : Main Components of Metasploit
===========================
[Question 1] : What is the name of the code taking advantage of a flaw on the target system?
[Answer] : Exploit
===========================
[Question 2] : What is the name of the code that runs on the target system to achieve the attacker's goal?
[Answer] : payload
===========================
[Question 3] : What are self-contained payloads called?
[Answer] : Singles
===========================
[Question 4] : Is "windows/x64/pingback_reverse_tcp" among singles or staged payload?
[Answer] : Singles
===========================
Task 3 : Msfconsole
===========================
[Question 1] : How would you search for a module related to Apache?
[Answer] : search Apache
===========================
[Question 2] : Who provided the auxiliary/scanner/ssh/ssh_login module?
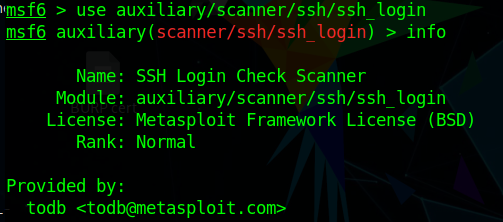
[Answer] : todb
===========================
Task 4 : Working with modules
===========================
[Question 1] : How would you set the LPORT value to 6666?
[Answer] : set LPORT 6666
===========================
[Question 2] : How would you set the global value for RHOSTS to 10.10.19.23 ?
[Answer] : setg RHOSTS 10.10.19.23
===========================
[Question 3] : What command would you use to clear a set payload?
[Answer] : unset PAYLOAD
===========================
[Question 4] : What command do you use to proceed with the exploitation phase?
[Answer] : exploit
===========================
Task 5 : Summary
No Answer Needed